Microsoft SentinelFormerly Azure Sentinel
Overview
What is Microsoft Sentinel?
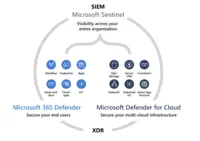
Microsoft Sentinel (formerly Azure Sentinel) is designed as a birds-eye view across the enterprise. It is presented as a security information and event management (SIEM) solution for proactive threat detection, investigation, and response.
How Microsoft Sentinel Differs From Its Competitors
Awards
Products that are considered exceptional by their customers based on a variety of criteria win TrustRadius awards. Learn more about the types of TrustRadius awards to make the best purchase decision. More about TrustRadius Awards
Popular Features
- Centralized event and log data collection (14)8.686%
- Correlation (14)8.484%
- Event and log normalization/management (14)8.282%
- Custom dashboards and workspaces (14)7.474%
Reviewer Pros & Cons
- Sentinel is by far the most efficient tool in supporting the highest number of solutions and products when it comes to data connection (or ingestion) ...
- 'Notebook' has always been a very hard to use feature for me in Sentinel. From my experience, there have been a very selective use cases for this feat...
Pricing
Azure Sentinel
$2.46
100 GB per day
$123.00
200 GB per day
$221.40
Entry-level set up fee?
- No setup fee
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Product Demos
Microsoft Sentinel: Monitoring health and integrity of analytics rules
Features
Product Details
- About
- Competitors
- Tech Details
- FAQs
What is Microsoft Sentinel?
Helps users to protect the digital estate: Secures the digital estate with scalable, integrated coverage for a hybrid, multicloud, multiplatform business.
Microsoft intelligence to Empower SOC: Optimizes SecOps with advanced AI, security expertise, and threat intelligence.
Detection, investigation and Response: A unified set of tools to monitor, manage, and respond to incidents.
Cost of ownership: A cloud-native SaaS solution to reduce infrastructural costs.
Microsoft Sentinel Features
Security Information and Event Management (SIEM) Features
- Supported: Centralized event and log data collection
- Supported: Correlation
- Supported: Event and log normalization/management
- Supported: Deployment flexibility
- Supported: Integration with Identity and Access Management Tools
- Supported: Custom dashboards and workspaces
- Supported: Host and network-based intrusion detection
- Supported: Log retention
- Supported: Data integration/API management
- Supported: Behavioral analytics and baselining
- Supported: Rules-based and algorithmic detection thresholds
- Supported: Response orchestration and automation
- Supported: Incident indexing/searching
Microsoft Sentinel Screenshots
Microsoft Sentinel Videos
Microsoft Sentinel Competitors
Microsoft Sentinel Technical Details
| Deployment Types | Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Unspecified |
| Mobile Application | No |